When it comes to website security, deploying a web application firewall (WAF) ruleset on the web server is crucial to protect your website.
These firewall rulesets prevent various types of web attacks, such as SQL injection, brute force, DDoS, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. This article lists the top web application firewall (WAF) rules set to deploy on your web server.
Implementing these Firewall / WAF rules right at the server-level firewall can block malicious attempts to exploit any vulnerabilities in your web applications and services. There are many types of web attacks that Web Application Firewall (WAF) rulesets help protect against:
- SQL Injection: Block attempts to inject malicious SQL queries into a website’s database, preventing manipulation of data or unauthorized access.
- Cross-Site Request Forgery (CSRF): Prevent attackers that force a user to perform actions on a website without their consent.
- Cross-Site Scripting (XSS): Block attempts to inject malicious scripts into web pages.
- Directory Traversal: Prevent access to restricted directories on the server, preventing potential data breaches or unauthorized file manipulation.
- Remote File Inclusion (RFI): WAF blocks attempts to remote file inclusion (RFI). Malicious files can lead to code execution and unauthorized access to sensitive server resources.
- Distributed Denial of Service (DDoS): WAF can analyze incoming traffic, detect patterns of malicious activity, and block or limit excessive traffic from the attacking sources.
- Brute Force Attacks: Detect and limit repeated login attempts, preventing password-guessing by brute force attempts.
- Command Injection: Block attempts to execute arbitrary commands and code execution on the server, preventing malicious actions.
- Clickjacking: WAF prevents clickjacking attacks by implementing security measures to block attempts to trick users into clicking on hidden elements.
- Zero-Day Attacks: They defend against previously unknown and any new emerging vulnerabilities or exploits.
Firewall Rule Sets in Web Servers and Control Panels
Web servers such as LiteSpeed, Nginx, Apache, etc. have different methods to deploy Firewall / WAF rulesets based on their specific configurations and capabilities.
For instance, in OpenLiteSpeed, you can utilize the ModSecurity module to implement WAF rulesets. This module provides a seamless integration and allows you to define rules to protect your web applications.
On the other hand, web control panels such as CyberPanel, Plesk, cPanel, WHM, etc. often come with built-in features for deploying firewall rulesets. These web control panels provide a simple interface where you can easily enable and configure WAF rulesets specific to your website’s needs. These features simplify the process of securing your web applications by offering a user-friendly way to manage and deploy the necessary rulesets.
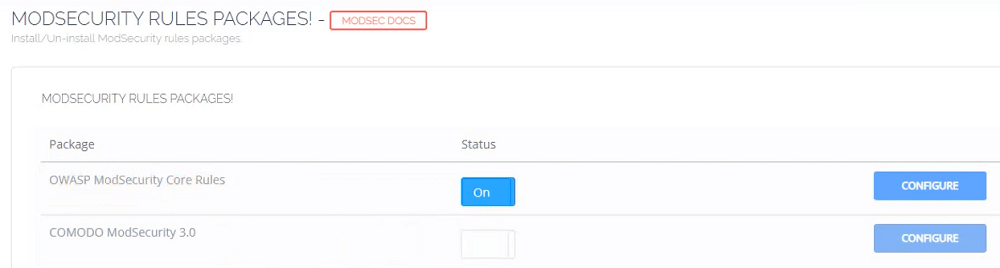
Also, it’s important to explore the documentation and resources as provided by your web server or control panel to understand the specific steps and options available for deploying Firewall / WAF rulesets for your website effectively.
List of the Top Firewall (WAF) Rule Sets to Deploy
Here are the top web application firewall (WAF) rulesets to deploy for your website.
OWASP ModSecurity Core Rule Set (CRS)
OWASP ModSecurity Core Rule Set (CRS) is a popular firewall (WAF) set of rules to protect web applications against various types of attacks, including SQL injection, remote file inclusion, cross-site scripting, and more.
What sets OWASP ModSecurity CRS apart is its open-source nature, which makes it highly customizable and adaptable. Security professionals have fine-grained control over the level of protection it offers. So, they can fine-tune the rule set to suit the specific requirements.
In addition, a dedicated community continuously updates the rules set to ensure that it stays up-to-date with emerging threats and vulnerabilities. This rule set is an excellent choice for those seeking community-driven, robust protection for their web applications.
Comodo Web Application Firewall (CWAF) Rule Set
The Comodo Web Application Firewall (CWAF) Rule Set provides robust protection for web applications or websites against a vast range of web attacks. It leverages the extensive threat intelligence network of Comodo. Also, it incorporates advanced behavioral analysis techniques to detect and block suspicious activities in real time. This is a great defense against zero-day attacks and application layer vulnerabilities.
Additionally, the CWAF rule set provides granular control over the security policies. It offers features such as blacklist monitoring, malware scanning, bot management, and virtual patching capabilities to address vulnerabilities before they can be exploited.
Cloudflare WAF Rules
Cloudflare’s Web Application Firewall (WAF) ruleset is just a part of Cloudflare’s cloud-based security platform. This is a scalable and powerful web firewall solution. Its global network of data centers allows it to provide low-latency protection against web application threats.
It offers protection against various types of attacks that include DDoS attacks, SQL injection, cross-site scripting, etc. Cloudflare’s firewall (WAF) leverages machine learning algorithms to identify suspicious traffic patterns, minimize false positives, and protect against automated bots. It also includes advanced rate-limiting capabilities and IP reputation features to prevent brute-force attacks and API abuse.
Additionally, Cloudflare’s WAF offers unique features such as CDN capabilities, making it a comprehensive firewall security and CDN solution for websites or web applications seeking both protection and performance.
Cloudflare comes with managed rulesets which are preconfigured rulesets that you can deploy for your website. Also, you can override their defaults, and create or manage your own custom rulesets. It depends on their specific Cloudflare products.
Akamai Kona Site Defender Rule Set
Akamai’s Kona Site Defender Rule Set is a key component of Akamai’s cloud security offerings. Moreover, It leverages Akamai’s global network of servers to ensure that traffic is routed efficiently and securely. This global presence enables Kona Site Defender to absorb and mitigate even massive Distributed Denial of Service (DDoS) attacks without impacting the performance of web applications.
It offers a unique feature known as “Edge Security”. This distinctive capability allows Kona Site Defender to provide web application security at the network’s edge, closer to the source of threats. By intercepting and mitigating attacks before they reach the origin server, Kona Site Defender significantly reduces the risk of application downtime and data breaches.
Imunify360 Firewall (WAF) Rules
Imunify360 Firewall (WAF) rules are known for their automated and proactive security approach. They provide comprehensive protection for Linux web servers.
It includes the WAF Rules Auto-Configurator. This innovative feature adjusts the firewall rules to specific sites based on the Content Management Systems (CMS) they utilize. For example, if your site runs WordPress, Imunify applies a set of rules optimized for WordPress protection, eliminating unnecessary rule overhead for other CMS platforms like Joomla or Drupal. This smart approach optimizes security without compromising server performance, striking a balance between robust protection and resource efficiency.
Moreover, Imunify360 offers comprehensive reporting and auditing capabilities, that allow administrators to gain insights into security compliance and events. Its user-friendly interface simplifies the management of security policies, which makes it an excellent choice for organizations seeking a user-centric approach to web application security.
Atomicorp Firewall (WAF) Rules
The Atomicorp Firewall (WAF) ruleset is designed for simplicity and flexibility. Its WAF rules offer a range of pre-configured security policies, which reduce the complexity of setup.
One distinctive feature is its support for containerized environments. It protects applications that you deploy in containerized environments, such as Docker and Kubernetes. Its ruleset can integrate with container orchestration tools, providing security that can scale alongside your application instances.
Additionally, it includes continuous threat intelligence updates, ensuring it can defend against the latest threats. It offers pre-configured security policies that align with various compliance standards like PCI DSS and HIPAA. This simplifies the process of meeting regulatory requirements. It also provides features such as host-based intrusion detection, log-based intrusion detection, and file integrity monitoring which extends beyond web applications to monitor the overall security of the host server.
Atomicorp focuses on straightforward implementation and has the ability to adapt to various hosting environments. This makes it a practical choice for organizations of all sizes.
Imperva WAF Rules
Imperva WAF includes CSRF protection, anti-automation, bot mitigation, and analytics capabilities. It employs machine learning algorithms to continuously analyze traffic patterns and generate custom signatures on demand. Having this dynamic approach, it can detect new attack methods promptly without relying solely on predefined signatures.
Imperva Runtime Protection secures application runtimes with a positive security model for detecting anomalies and threats. It shields against internal and zero-day attacks.
The ThreatRadar network from Imperva aggregates data across users to identify emerging attacks. Imperva provides on-going rule updates and management capabilities like dynamic profiling and tunable sensitivity levels.
Conclusion
Deploying web application firewall (WAF) rules is vital to safeguard against various attacks on your website. A robust firewall / WAF ruleset acts as a proactive defense mechanism. It’s important to stay updated with the latest firewall / WAF ruleset versions. Also, monitor and fine-tune the rules regularly to ensure optimal protection for your website.
Additionally, to further improve your website security, it is crucial to have multiple layers of protection and incorporate secure coding practices. For example, if you have a WordPress website, install a captcha security plugin, always sanitize any input data properly, make use of nonce, and do appropriate permission checks.